Kaspersky Labs has detected a new virus outbreak, caused by Netsky.d, the fourth version of the Internet worm Netsky (also known as Moodown.d). To date, numerous notifications of infected machines have already been received. Given this, Kaspersky Labs recommends all users to update their...
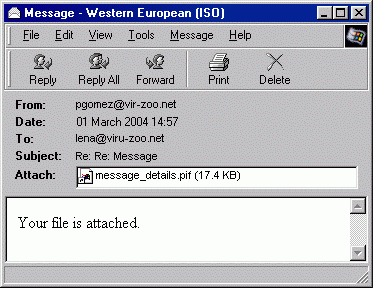
Netsky.d spreads as an attachment to email messages. Infected messages come in a wide range of forms; the worm randomly selects the message heading from 25 possible headings, the message body from a list of 6 possible texts, and the attachment name from a selection of 21.
The attachment is a standard EXE program, of approximately 17KB, but the attached file will have a fictitious .PIF extension. If a user is thoughtless enough to execute this file, the worm installs itself on the system and begins propagation.
During installation Netsky.d copies itself under the name WINLOGON.EXE to the Windows directory and registers this file in the system registry auto-run key. This ensures that the worm will be activated every time the operating system is started.
In order to send messages, the worm scans files with extensions of the most popular Internet applications (e.g. .wab, .eml, .doc, .html, .msg, etc.), harvests email addresses, and, unnoticed by the owner of the computer, sends copies of itself to these addresses. It should be noted that the worm uses its own inbuilt SMTP-engine, thus avoiding the use of the email client installed on the victim computer. In this way, Netsky.d propagates via 23 proxy servers located across the globe.
The worm has several payloads; specifically, it deletes the keys of another Internet worm, Mydoom, from the system registry, and attempts to terminate Kaspersky Anti-Virus.
Protection against Netsky.d has already been added to the Kaspersky® Anti-Virus database.
More detailed information about Netsky.d can be found in the Kaspersky Virus Encyclopaedia.
