Experts at Kaspersky Lab have detected a new variant of the now notorious malicious program GPCode
Experts at Kaspersky Lab have detected a new variant of the now notorious malicious program GPCode. The program is classed as Ransomware, i.e. it encrypts data on an infected computer and threatens to delete it if the user refuses to pay a ransom. This time the cybercriminals behind the program have chosen a new method of payment: they demand $125 in Ukash pre-paid vouchers. “It seems the criminals are moving away from conventional money transfers and now prefer pre-paid vouchers instead,” said Nicolas Brulez, Senior Malware Researcher with the Global Research & Analysis Team who is based France. He pointed out that this was the second incident within a week in which a new Ransomware program had made use of Ukash pre-paid vouchers.
Kaspersky Lab’s experts are carefully researching possible methods for restoring data on compromised machines; meanwhile however, files encrypted by the new version of GPCode cannot be recovered.
The GPCode Trojan first appeared on the threat landscape back in 2004. In November 2010, experts noted considerably more elaborate program code that made use of strong cryptographic algorithms. Before deleting data, the version detected last November overwrote information in files in such a way as to make it impossible for standard data-recovery software to restore a user’s data.
Trojan-Ransom.Win32.Gpcode.bn, which was detected by Kaspersky Lab’s experts last week infects computers using drive-by downloads that occur when an infected website is visited. The Trojan then starts running in the system, encrypting data without the user’s knowledge. The following message is then displayed:
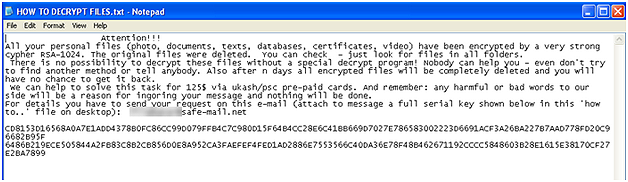
At this point, the hard drives are being scanned for files to encrypt. The file extensions used to determine whether a file is to be encrypted or not are kept in an encrypted configuration file. This means the GPCode Ransomware Trojan is easily updated with a new configuration file.
If you think your computer is infected, Kaspersky Lab’s experts recommend that you do not change anything on your system as it may prevent potential data recovery later on. Desperate situations can sometimes require desperate measures, so don't hesitate to turn off your PC or pull out the power cable if that is the quickest method to prevent malware damage! “We haven't seen any evidence of a time-based file deleting mechanism despite claims by the malware writer that files are deleted after ‘N’ number of days,” writes Nicolas Brulez in his latest blog post dedicated to the new version of GPCode. “Nevertheless, it is better to avoid any changes that could be made to the file system which, for example, may be caused by rebooting the computer.”
The encrypted files cannot be recovered because of the strong encryption algorithm employed. At present, the only way to recover your files is via backups. Meanwhile, Kaspersky Lab’s experts are continuing their careful analysis of the new version of GPCode and investigating possible ways to restore data on compromised machines.
Users of Kaspersky Lab products are fully protected against this malicious program – the threat was detected proactively thanks to the Kaspersky Security Network.
